Introduction
Enterprise wireless LANs (WLANs) have expanded rapidly over the past few years, moving from small hotspot style deployments in conference rooms and other common areas, to pervasive enterprise-wide deployments that span the campus, branch office, telecommuters and even nomadic remote offices. As these wireless networks grow in size, their scalability is primarily determined by the underlying architecture for of the wireless LAN and its interworking with the wired architecture.
Enterprise WLAN design has evolved from a distributed to a centralized model. It is clear that centralized WLAN architectures are here to stay and will be the dominant method of building enterprise wireless networks. However, not all centralized architectures are created equal. Customers are faced with two architectural options even with centralized architectures. One option is to embed centralized WLAN capabilities into the existing network infrastructure. This requires an upgrade to the fixed, or wired, edge of the network to address the challenges associated with mobility. The other option is to create a new mobile edge that extends beyond the existing fixed edge and allows users to connect from any location, at any time. A mobile edge requires an overlay network model that delivers mobile connectivity across the corporate network and the public Internet.
Figure 1. Mobile Edge Architecture – Common User Experience across LAN, WAN and Internet
Determining which products and solutions available today can address this fundamental architectural difference can be difficult since most of the industry rhetoric seems similar. One key area of differentiation is scalability. Traditional scalability metrics of centralized wireless LAN architectures have focused on controller throughput and the number of thin access points supported by centralized WLAN controllers. While these are important metrics, real-world experience in deploying high-end enterprises has yielded fresh insight into scaling requirements for wireless LANs. The challenges of scaling enterprise wireless LANs can be categorized by three key enterprise WLAN categories
* Campus wireless LANs that have hundreds to thousands of users and devices,
* Branch office wireless LANs that have between ten and one hundred users and devices, and
* Telecommuter and nomadic office wireless LANs that have between one and ten users.
Scaling Campus Wireless LANs
As the enterprise workforce becomes increasingly mobile, user counts on campus wireless LANs are constantly on the rise, and with the proliferation of Wi-Fi-equipped personal handheld devices, device counts are increasing even more rapidly. The key challenges of scaling a campus wireless LAN are caused by the density of users and devices, instantaneous loads caused during peak hour usage, and the mobility of users between different areas on the campus. The associated technical challenges relate to the scaling of RF capacity, AAA services and VLAN architecture for mobile networks.
Scaling RF Capacity with Multi-channel RF Architecture
All centralized WLAN architectures today incorporate some level of RF management functionality, which is designed to automate the site survey process. However, in most implementations, RF management is limited to pre-planning, and makes use of heavy duty RF planning software. Other vendors claim to eliminate the entire planning process by moving to a single channel architecture. Both approaches leave much to be desired when it comes to delivering high-capacity wireless LANs.
In the first instance, planning access point placement based on building materials and other RF planning models is fundamentally flawed because the RF characteristics are dynamic and change constantly. This results in a failure to adjust to ambient RF conditions or, worse yet, in sub-optimal results, when assumptions regarding building materials and other variables are flawed. Single channel architectures, while eliminating the planning problem, introduce an issue related to client density. When all clients are operating on the same channel, co-channel interference increases significantly, resulting in poor performance.
Multi-channel RF architectures are inherently better suited for high density usage since they utilize all available channels in the spectrum to reduce co-channel interference. However, multi-channel architectures must be completely automated from a deployment standpoint. New techniques such as Adaptive Radio Management (ARM) are emerging in the industry to completely automate the deployment of multi-channel RF architectures and reduce co-channel interference. This leads to much higher RF capacity and better RF performance of WLAN networks.
As density increases, enterprises are employing strategies to migrate to 802.11a on the 5GHz band which has 4-5 times more capacity than the 2.4GHz band. The 5GHz band is also inherently much cleaner with respect to interference, yielding better and more consistent channel performance. The 2.4GHz band will continue to be the first choice for equipment manufacturers of most handheld mobile devices such as Vo-Fi phones, PDAs, dual-mode phones, barcode scanners and active RFID tags because of the greater maturity, lower cost, and lower power demands of 802.11b/g silicon. However, laptop manufacturers have finally caught up and are now implementing new power management efficiencies and adding support for 802.11a. The newer laptops with 802.11a/b/g network interface cards auto select, and, wherever possible, opt for, the 5GHz band. This, in turn, is resulting in a hybrid approach, using the 5GHz band for laptops and the 2.4GHz band for other handheld devices.
In addition, enterprises are increasing using a four-channel architecture in the 2.4GHz band instead of the traditional three channel approach, as the extra channel yields additional capacity, especially valuable in dense deployments.
Figure 2. Multi-channel RF Delivers Up To 3 Times the Capacity of a Single-channel RF Architecture
Scaling AAA Services with Hardware Acceleration of 802.1X Authentication
Even with additional RF capacity and a successful 802.11 association, devices in large enterprise networks may still be unable to connect to the network. This is often the result of heavy loads on the back-end authentication, authorization and accounting (AAA) server. This situation is being compounded with the implementation of new authentication practices as part of 802.11i.
802.11i, which requires all users and devices to authenticate to the WLAN using the 802.1X authentication protocol, is established as an industry standard best practice for securing enterprise WLANs, 802.11i The National Institute of Standards and Technology (NIST), responsible for setting government standards has, in fact, mandated the use of 802.11i in securing WLAN networks.
Traditionally, in centralized WLAN architectures, the controller only serves as an authenticator in the 802.1X authentication process. The actual AAA transaction of verifying a username and password combination is carried inside an encrypted TLS tunnel between the wireless client and the AAA server. Typical tunnel types used today are PEAP and EAP-TLS, with PEAP as the dominant method.
The introduction of 802.11i forces AAA servers to take on an even greater computational burden.
The AAA server is given the responsibility of both terminating encrypted authentication network protocols such as EAP-PEAP, as well as generating the encryption keys that are used by WLAN clients and access points for secure wireless 802.11 communications.
As user density and the number of login requests per second goes up, the backend AAA server’s ability to process cryptographic information with consistent response times while simultaneously authenticating and authorizing users becomes a bottleneck. Users in heavily loaded wireless networks end up with slow, variable response times during network login, and may even experience network disconnects due to timeouts. Customers who have experienced this problem end up having to set up multiple AAA proxy servers to scale AAA processing capacity in the network. The extra proxy servers and associated network redesigns increase network complexity and add both capital and operational expense.
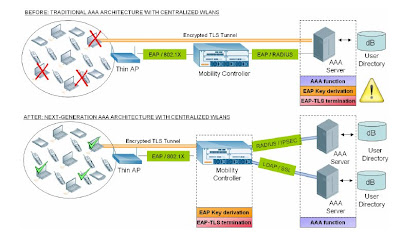
Solutions to this problem are emerging from some centralized wireless LAN vendors whose WLAN controllers are architecturally capable of absorbing the fixed, but immense, overhead of the 802.1X authentication process. These controllers incorporate purpose-built hardware encryption processors to terminate the PEAP/TLS tunnels and centrally compute the crypto keys for secure wireless communications, offloading the back-end AAA server from this significant processing burden and leaving it free to perform the tasks of AAA. This approach, known as AAA FastConnect, results in over 1,000 authentications per second – a tenfold increase – eliminating the issue of slow connect times and failed login attempts.
AAA FastConnect not only results in faster and more predictable connect times, but also greatly simplifies the integration of secure WLANs with various back-end servers. In traditional AAA architectures, back-end AAA servers must be upgraded to handle 802.11i security since centralized controllers are just a pass through relay in the authentication phase. With AAA FastConnect, a mobility controller can interoperate directly with a AAA server using RADIUS or LDAP since all AAA related 802.11i security requirements are absorbed into the mobility controller itself. Furthermore, RADIUS packets can be encrypted in an IPSec tunnel, while LDAP transactions can be encrypted in SSL to keep the entire AAA transaction encrypted end-to-end. Such flexibility is not possible with traditional AAA architectures. This enables the entire WLAN to operate as a secure overlay, without requiring any additional investment to upgrade or add security to the wired network and cost-effectively solving the scalability problem.
Hernández Caballero Indiana
Asignatura: CRF
Fuente:http://www.wit.co.th/pdf/Aruba/Scaling-Enterprise-Wireless_LAN.pdf


No hay comentarios:
Publicar un comentario